FCP - FortiGate 7.4 Administrator
Last Update 1 month ago
Total Questions : 89
FCP - FortiGate 7.4 Administrator is stable now with all latest exam questions are added 1 month ago. Incorporating FCP_FGT_AD-7.4 practice exam questions into your study plan is more than just a preparation strategy.
FCP_FGT_AD-7.4 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through FCP_FGT_AD-7.4 dumps allows you to practice pacing yourself, ensuring that you can complete all FCP - FortiGate 7.4 Administrator practice test within the allotted time frame.
Refer to the exhibit.

The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.
What are two solutions for satisfying the requirement? (Choose two.)
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors.
What is the reason for the certificate warning errors?
Refer to the exhibits, which show the firewall policy and an antivirus profile configuration.
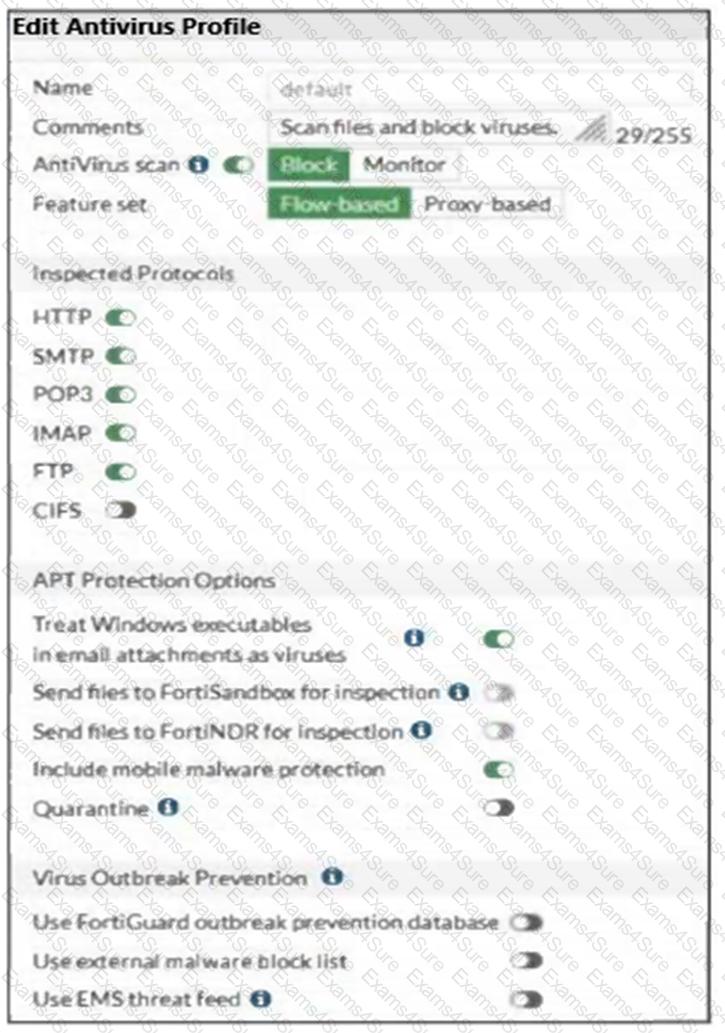
Why is the user unable to receive a block replacement message when downloading an infected file for the first time?
Refer to the exhibit.
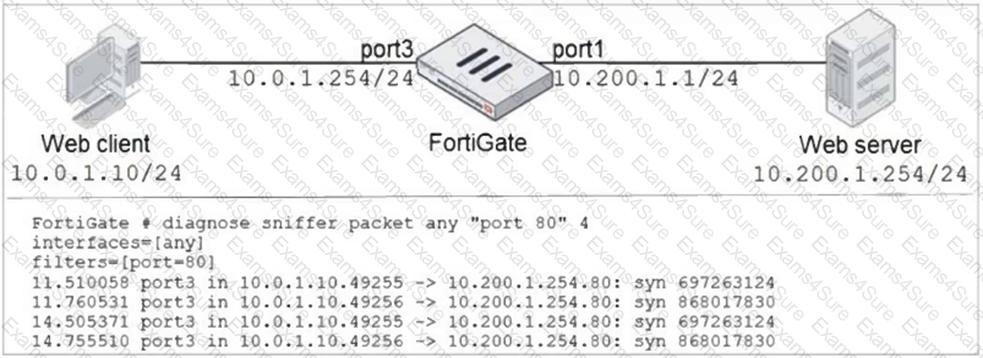
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
Refer to the exhibit.

The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name.
FortiGate allows the traffic according to policy ID 1. This is the policy that allows SD-WAN traffic.
Despite these settings the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows.
What can be the reason?
An administrator is configuring an IPsec VPN between site A and site В. The Remote Gateway setting in both sites has been configured as Static IP Address.
For site A, the local quick mode selector is 192.168.1.0/24 and the remote quick mode selector is 192.168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
Refer to the exhibit.

Which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules?
Refer to the exhibits.
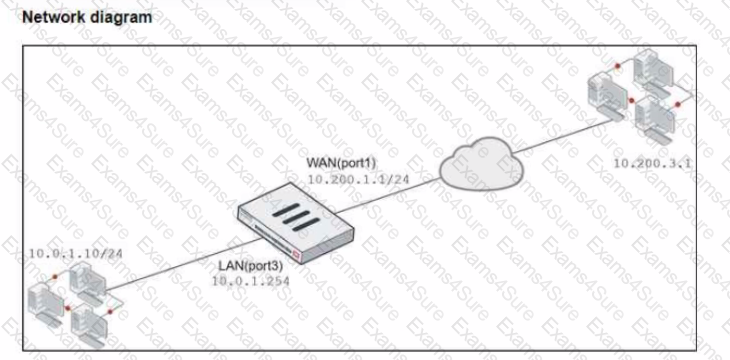
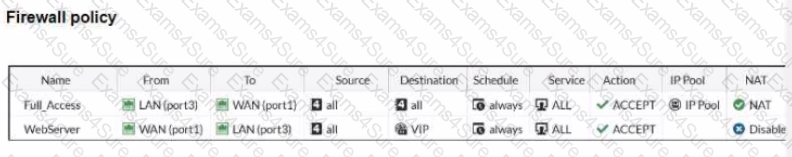
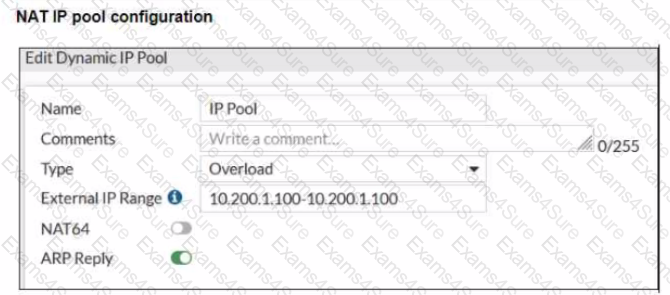
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall policies configuration VIP configuration and IP pool configuration on the FortiGate device
The WAN (port1) interface has the IP address 10.200. l. 1/24 The LAN (port3) interface has the IP address 10.0.1.254/24
The first firewall policy has NAT enabled using the IP pool The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT (SNAT) the internet traffic coming from a workstation with the IP address 10.0.1.10?
Refer to the exhibit.
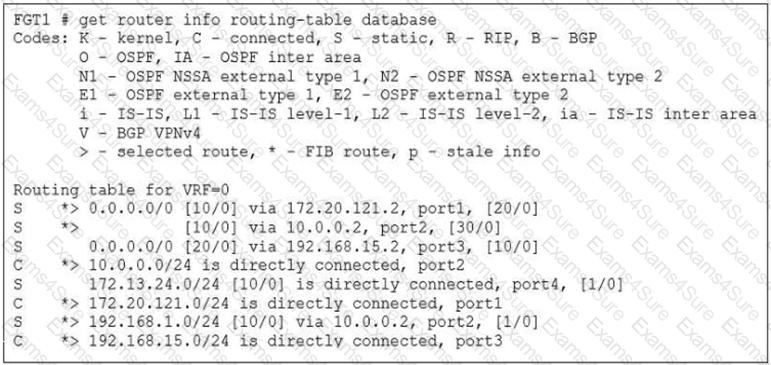
Based on the routing database shown in the exhibit which two conclusions can you make about the routes? (Choose two.)
Refer to the exhibits, which show the firewall policy and the security profile for Facebook.
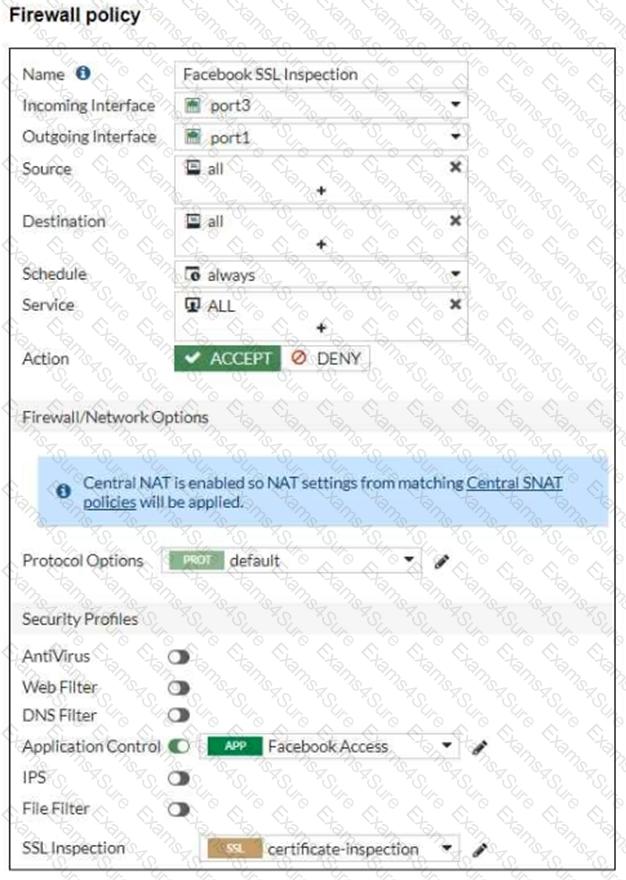
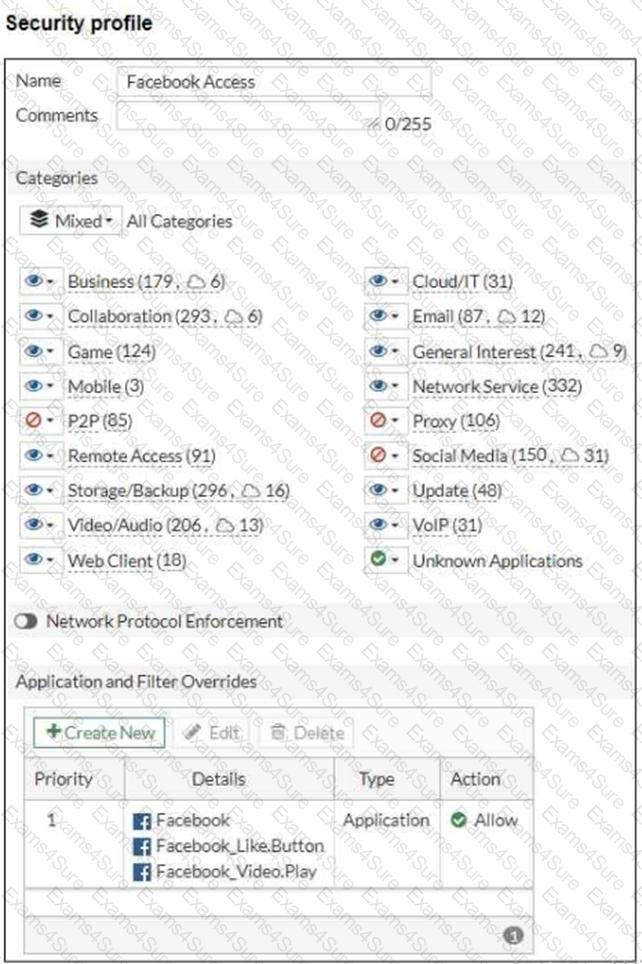
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the configuration must you change to resolve the issue?


TESTED 31 Mar 2025
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.