CompTIA Cloud+ (2025)
Last Update 2 months ago
Total Questions : 229
CompTIA Cloud+ (2025) is stable now with all latest exam questions are added 2 months ago. Incorporating CV0-004 practice exam questions into your study plan is more than just a preparation strategy.
CV0-004 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through CV0-004 dumps allows you to practice pacing yourself, ensuring that you can complete all CompTIA Cloud+ (2025) practice test within the allotted time frame.
Which of the following communication methods between on-premises and cloud environments would ensure minimal-to-low latency and overhead?
A company just learned that the data in its object storage was accessed by an unauthorized party. Which of the following should the company have done to make the data unusable?
An organization's critical data was exfiltrated from a computer system in a cyberattack. A cloud analyst wants to identify the root cause and is reviewing the following security logs of
a software web application:
"2021/12/18 09:33:12" "10. 34. 32.18" "104. 224. 123. 119" "POST / login.php?u=administrator&p=or%201%20=1"
"2021/12/18 09:33:13" "10.34. 32.18" "104. 224. 123.119" "POST /login. php?u=administrator&p=%27%0A"
"2021/12/18 09:33:14" "10. 34. 32.18" "104. 224. 123. 119" "POST /login. php?u=administrator&p=%26"
"2021/12/18 09:33:17" "10.34. 32.18" "104. 224. 123.119" "POST / login.php?u=administrator&p=%3B"
"2021/12/18 09:33:12" "10.34. 32. 18" "104. 224. 123. 119" "POST / login. php?u=admin&p=or%201%20=1"
"2021/12/18 09:33:19" "10.34.32.18" "104. 224. 123.119" "POST / login. php?u=admin&p=%27%0A"
"2021/12/18 09:33:21" "10. 34. 32.18" "104.224. 123.119" "POST / login. php?u=admin&p=%26"
"2021/12/18 09:33:23" "10. 34. 32.18" "104. 224. 123.119" "POST / login. php?u=admin&p=%3B"
Which of the following types of attacks occurred?
A cloud server needs to automatically allocate more resources during sudden peak times. This allocation does not need to occur in regular intervals. Which of the following scaling
approaches should be used?
A cloud solutions architect is designing a VM-based solution that requires reducing the cost as much as possible. Which of the following solutions will best satisfy this requirement?
An organization is hosting a seminar with eight individuals who need to connect to their own dedicated VM. The technician used the following VM configurations:
IP address: DHCP
NIC: 1Gbps
Network: 10.1.10.0/29
Several users are unable to access their VMs. Which of the following best describes the reason?
Which of the following refers to the idea that data should stay within certain borders or territories?
A list of CVEs was identified on a web server. The systems administrator decides to close the ports and disable weak TLS ciphers. Which of the following describes this vulnerability management stage?
Which of the following is a customer be responsible for in a provider-managed database service? (Select two).
A cloud administrator wants to provision a host with two VMs. The VMs require the following:
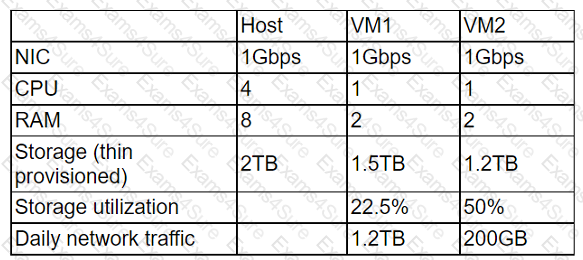
After configuring the servers, the administrator notices that during certain hours of the day, the performance heavily degrades. Which of the following is the best explanation?


TESTED 03 Apr 2025
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.