CompTIA CyberSecurity Analyst CySA+ Certification Exam
Last Update 3 days ago
Total Questions : 424
CompTIA CyberSecurity Analyst CySA+ Certification Exam is stable now with all latest exam questions are added 3 days ago. Incorporating CS0-003 practice exam questions into your study plan is more than just a preparation strategy.
CS0-003 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through CS0-003 dumps allows you to practice pacing yourself, ensuring that you can complete all CompTIA CyberSecurity Analyst CySA+ Certification Exam practice test within the allotted time frame.
Which of the following attributes is part of the Diamond Model of Intrusion Analysis?
Given the following CVSS string-
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/3:U/C:K/I:K/A:H
Which of the following attributes correctly describes this vulnerability?
During a scan of a web server in the perimeter network, a vulnerability was identified that could be exploited over port 3389. The web server is protected by a WA
F.
Which of the following best represents the change to overall risk associated with this vulnerability?An incident response analyst is investigating the root cause of a recent malware outbreak. Initial binary analysis indicates that this malware disables host security services and performs cleanup routines on it infected hosts, including deletion of initial dropper and removal of event log entries and prefetch files from the host. Which of the following data sources would most likely reveal evidence of the root cause?
(Select two).
An analyst suspects cleartext passwords are being sent over the network. Which of the following tools would best support the analyst's investigation?
Which of the following is the best metric for an organization to focus on given recent investments in SIEM, SOAR, and a ticketing system?
While reviewing web server logs, a security analyst discovers the following suspicious line:
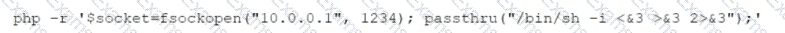
Which of the following is being attempted?
A company was able to reduce triage time by focusing on historical trend analysis. The business partnered with the security team to achieve a 50% reduction in phishing attempts year over year. Which of the following action plans led to this reduced triage time?
An analyst is suddenly unable to enrich data from the firewall. However, the other open intelligence feeds continue to work. Which of the following is the most likely reason the firewall feed stopped working?
Following an incident, a security analyst needs to create a script for downloading the configuration of all assets from the cloud tenancy. Which of the following authentication methods should the analyst use?


TESTED 26 Mar 2025
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.