CompTIA SecurityX Certification Exam
Last Update 1 week ago
Total Questions : 187
CompTIA SecurityX Certification Exam is stable now with all latest exam questions are added 1 week ago. Incorporating CAS-005 practice exam questions into your study plan is more than just a preparation strategy.
CAS-005 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through CAS-005 dumps allows you to practice pacing yourself, ensuring that you can complete all CompTIA SecurityX Certification Exam practice test within the allotted time frame.
Which of the following best explains the importance of determining organization risk appetite when operating with a constrained budget?
An organization is implementing Zero Trust architecture A systems administrator must increase the effectiveness of the organization's context-aware access system. Which of the following is the best way to improve the effectiveness of the system?
A security architect for a global organization with a distributed workforce recently received funding lo deploy a CASB solution Which of the following most likely explains the choice to use a proxy-based CASB?
A company recently experienced aransomware attack. Although the company performssystems and data backupon a schedule that aligns with itsRPO (Recovery Point Objective) requirements, thebackup administratorcould not recovercritical systems and datafrom its offline backups to meet the RPO. Eventually, the systems and data were restored with information that wassix months outside of RPO requirements.
Which of the following actions should the company take to reduce the risk of a similar attack?
A company finds logs with modified time stamps when compared to other systems. The security team decides to improve logging and auditing for incident response. Which of the following should the team do to best accomplish this goal?
A security analyst is reviewing the following vulnerability assessment report:
192.168.1.5, Host = Server1, CVSS 7.5, Web Server, Remotely Executable = Yes, Exploit = Yes
205.1.3.5, Host = Server2, CVSS 6.5, Bind Server, Remotely Executable = Yes, Exploit = POC
207.1.5.7, Host = Server3, CVSS 5.5, Email Server, Remotely Executable = Yes, Exploit = Yes
192.168.1.6, Host = Server4, CVSS 9.8, Domain Controller, Remotely Executable = Yes, Exploit = Yes
Which of the following should be patched first to minimize attacks against internet-facing hosts?
A security analyst is reviewing the following authentication logs:
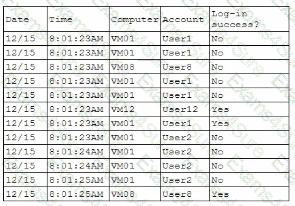
Which of the following should the analyst do first?
During a gap assessment, an organization notes that OYOD usage is a significant risk. The organization implemented administrative policies prohibiting BYOD usage However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following solutions should the organization implement to b»« reduce the risk of OYOD devices? (Select two).
Developers have been creating and managing cryptographic material on their personal laptops fix use in production environment. A security engineer needs to initiate a more secure process. Which of the following is the best strategy for the engineer to use?
An organization that performs real-time financial processing is implementing a new backup solution. Given the following business requirements:
The backup solution must reduce the risk of potential backup compromise.
The backup solution must be resilient to a ransomware attack.
The time to restore from backups is less important than backup data integrity.
Multiple copies of production data must be maintained.
Which of the following backup strategies best meets these requirements?


TESTED 04 Apr 2025
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.