CompTIA A+ Certification Core 2 Exam
Last Update 1 week ago
Total Questions : 788
CompTIA A+ Certification Core 2 Exam is stable now with all latest exam questions are added 1 week ago. Incorporating 220-1102 practice exam questions into your study plan is more than just a preparation strategy.
220-1102 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through 220-1102 dumps allows you to practice pacing yourself, ensuring that you can complete all CompTIA A+ Certification Core 2 Exam practice test within the allotted time frame.
Which of the following is command options is used to display hidden files and directories?
A user is setting up backups on a workstation. The user wants to ensure that the restore process is as simple as possible. Which of the following backup types should the user select?
A technician is installing software on a user's workstation. The installation fails due to incompliance with the HCL. Which of the following components is most likely causing the installation to fail? (Select two).
A customer wants to make sure the data is protected and secure on a Windows laptop's hard drive. Which of the following is the best solution?
A technician is trying to connect to a user's laptop in order to securely install updates. Given the following information about the laptop:

Which of the following should the technician do to connect via RDP?
A technician has verified a computer is infected with malware. The technician isolates the system and updates the anti-malware software. Which of the following should the technician do next?
As a corporate technician, you are asked to evaluate several suspect email messages on
a client's computer. Corporate policy requires he following:
. All phishing attempts must be reported.
. Future spam emails to users must be prevented.
INSTRUCTIONS
Review each email and perform the
following within the email:
. Classify the emails
. Identify suspicious items, if applicable, in each email
. Select the appropriate resolution
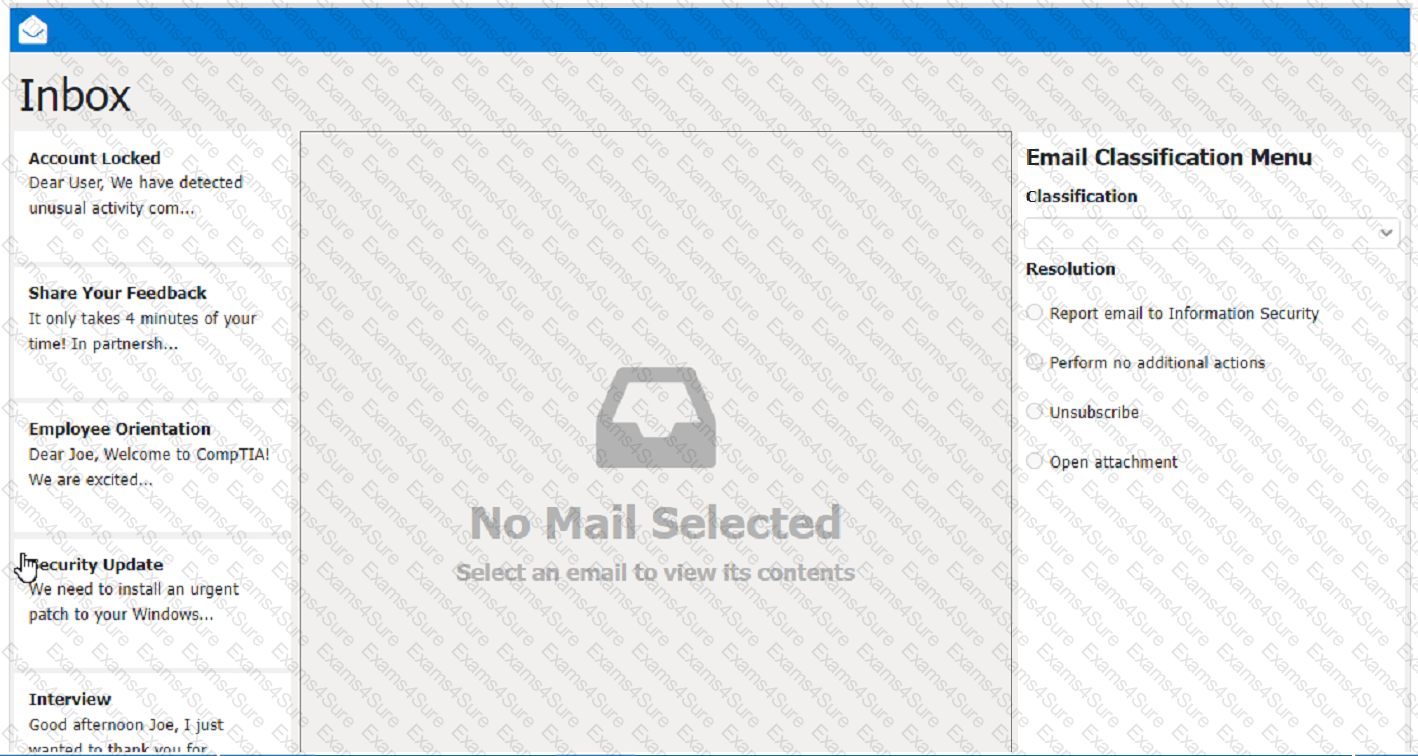
A user clicks a link in an email. A warning message in the user's browser states the site's certificate cannot be verified. Which of the following is the most appropriate action for a technician to take?
Which of the following is used to ensure users have the appropriate level of access to perform their job functions?
Which of the following environmental factors are most important to consider when planning the configuration of a data center? (Select two).
A systems administrator is troubleshooting network performance issues in a large corporate office. The end users report that traffic to certain internal environments is not stable and often drops. Which of the following command-line tools can provide the most detailed information for investigating the issue further?
A large organization is researching proprietary software with vendor support for a multiuser environment. Which of the following EULA types should be selected?
Which of the following is the best way to limit the loss of confidential data if an employee's company smartphone is lost or stolen?
A user wants to acquire antivirus software for a SOHO P
C.
A technician recommends a licensed software product, but the user does not want to pay for a license. Which of the following license types should the technician recommend?A computer technician is investigating a computer that is not booting. The user reports that the computer was working prior to shutting it down last night. The technician notices a removable USB device is inserted, and the user explains the device is a prize the user received in the mail yesterday. Which of the following types of attacks does this describe?


TESTED 13 Apr 2025
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.