Cisco Certified Network Associate
Last Update 3 weeks ago
Total Questions : 1005
Cisco Certified Network Associate is stable now with all latest exam questions are added 3 weeks ago. Incorporating 200-301 practice exam questions into your study plan is more than just a preparation strategy.
200-301 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through 200-301 dumps allows you to practice pacing yourself, ensuring that you can complete all Cisco Certified Network Associate practice test within the allotted time frame.
What is the primary different between AAA authentication and authorization?
Which protocol does an access point use to draw power from a connected switch?
An office has 8 floors with approximately 30-40 users per floor What command must be configured on the router Switched Virtual Interface to use address space efficiently?
Refer to the exhibit.
The entire contents of the MAC address table are shown. Sales-4 sends a data frame to Sales-1.
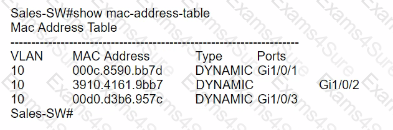
What does the switch do as it receives the frame from Sales-4?
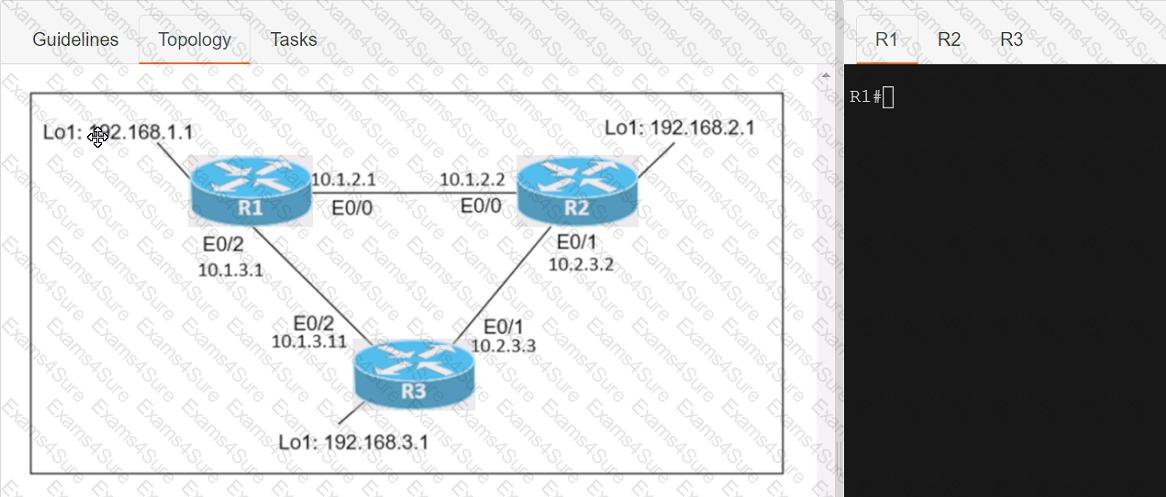
Connectivity between three routers has been established, and IP services must be configured jn the order presented to complete the implementation Tasks assigned include configuration of NAT, NTP, DHCP, and SSH services.
1. All traffic sent from R3 to the R1 Loopback address must be configured for NAT on R2. All source addresses must be translated from R3 to the IP address of Ethernet0/0 on R2, while using only a standard access list named NAT To verify, a ping must be successful to the R1 Loopback address sourced from R3. Do not use NVI NAT configuration.
2. Configure R1 as an NTP server and R2 as a client, not as a peer, using the IP address of the R1 Ethernet0/2 interface. Set the clock on the NTP server for midnight on January 1, 2019.
3. Configure R1 as a DHCP server for the network 10.1.3.0/24 in a pool named TEST. Using a single command, exclude addresses 1-10 from the range. Interface Ethernet0/2 on R3 must be issued the IP address of 10.1.3.11 via DHCP.
4. Configure SSH connectivity from R1 to R3, while excluding access via other remote connection protocols. Access for user root and password Cisco must be set on router R3 using RSA and 1024 bits. Verify connectivity using an SSH session from router R1 using a destination address of 10.1.3.11. Do NOT modify console access or line numbers to accomplish this task.
Which WLC management connection type is vulnerable to man-in-the-middIe attacks?
Drag and drop the AAA lerms from the left onto the descriptions on the right.

Which Windows command is used instead of the route print command to display the contents of the IP routing table?
What differentiates device management enabled by cisco DNA center from traditional campus device management?
An engineer is configuring a switch port that is connected to a VoIP handset. Which command must the engineer configure to enable port security with a manually assigned MAC address of abod-bod on voice VLAN 4?
Drag and drop the statements about access-point modes from the left onto the corresponding modes on the right.

A network engineer must configure an interface with IP address 10.10.10.145 and a subnet mask equivalent to 11111111.11111111.11111111.11111000. Which subnet mask must the engineer use?
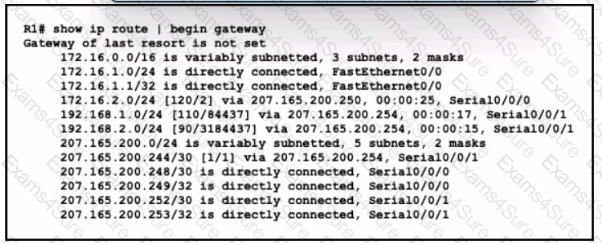
Refer to the exhibit. Drag and drop the learned prefixes from the left onto the preferred route methods from which they were learned on the right.
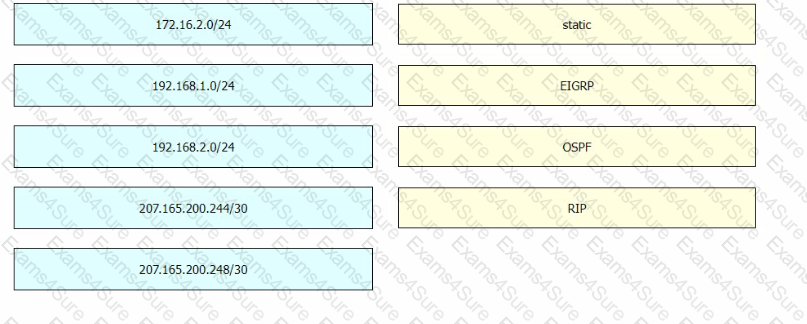
Refer to the exhibit.
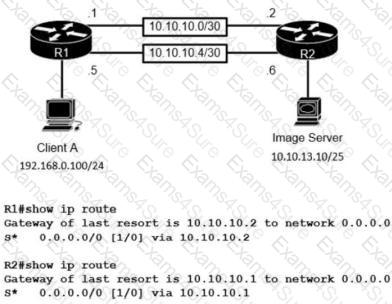
The image server and client A are running an application that transfers an extremely high volume of data between the two. An engineer is configuring a dedicated circuit between R1 and R2. Which set of commands must the engineer apply to the routers so that only traffic between the image server and client A is forces to use the new circuit?
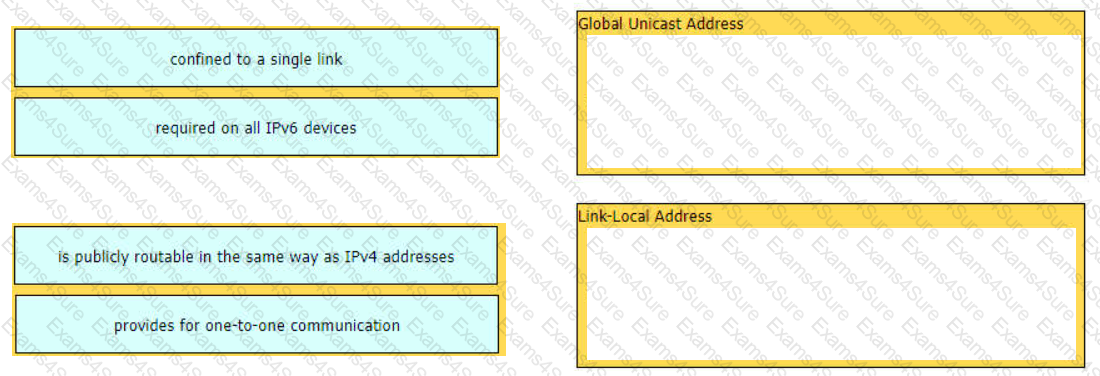
Drag and drop the characteristic from the left onto the IPv6 address type on the right.


TESTED 27 Mar 2025
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.