Dell Security Foundations Achievement
Last Update 1 month ago
Total Questions : 20
Dell Security Foundations Achievement is stable now with all latest exam questions are added 1 month ago. Incorporating D-SF-A-24 practice exam questions into your study plan is more than just a preparation strategy.
D-SF-A-24 exam questions often include scenarios and problem-solving exercises that mirror real-world challenges. Working through D-SF-A-24 dumps allows you to practice pacing yourself, ensuring that you can complete all Dell Security Foundations Achievement practice test within the allotted time frame.
During analysis, the Dell Services team found outdated applications and operating systems with missing security patches. To avert potential cyberattacks, Dell recommends application and operating system hardening measures.
Why is security hardening important for
A.
R.T.I.E .?The cybersecurity team created a detailed security incident management procedures training program to manage any probable incidents atA .R.T.I.
E.
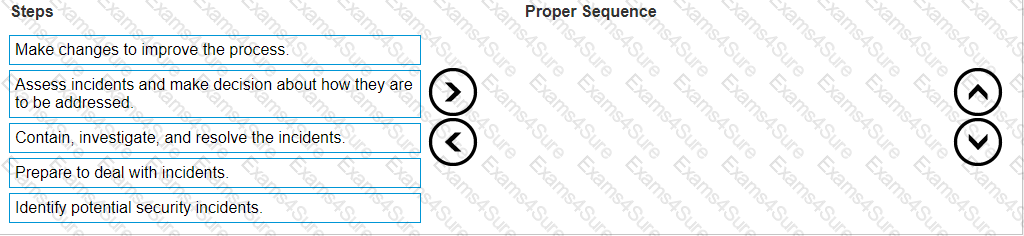
Arrange the steps in the proper sequence to best manage cybersecurity incidents.
During the analysis, the threat intelligence team disclosed that attackers not only encrypted files, but also attempted to encrypt backups and shared, networked, and cloud drives.
Which type of ransomware is used for this attack?
AnA .R.T.I.
E.
employee received an email with an invoice that looks official for $200 for a one-year subscription. It clearly states: "Please do not reply to this email," but provides a Help and Contact button along with a phone number.What is the type of risk if the employee clicks the Help and Contact button?
Dell Services team cannot eliminate all risks, but they can continually evaluate the resilience and preparedness ofA .R.T.I.
E.
by using the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF).Match the core NIST CSF component functions with the description that the Dell Services team would have recommended toA .R.T.I.
E.

An externalA .R.T.I.
E.
user requires access to sensitive resources and data.Which authentication technique should be best recommended to provide access to this business user?


TESTED 12 Mar 2025
Hi this is Romona Kearns from Holland and I would like to tell you that I passed my exam with the use of exams4sure dumps. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Our all material is important and it will be handy for you. If you have short time for exam so, we are sure with the use of it you will pass it easily with good marks. If you will not pass so, you could feel free to claim your refund. We will give 100% money back guarantee if our customers will not satisfy with our products.